In the Authentication tab, you can define the settings regarding the Authentication service (Identity server). The Authentication service is responsible for the user login and user resolve tasks. It is elementary to set up for every application, as it defines how you authenticate with the system.
More about these can be found at Authentication.
The tables below the screenshots provide guidance on what to fill in the fields.
When using an external server, make sure you enter the correct server Name and Port.
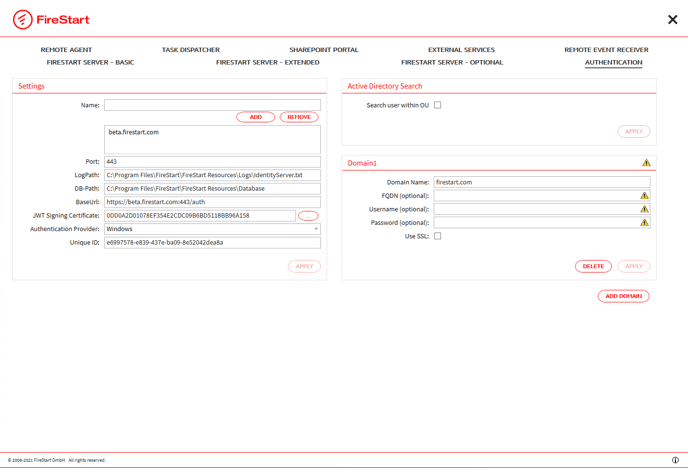
| Settings | |
|
Name: |
Name of the IdentityServer host (FQDN). Make sure to add the alias addresses as well, if the Identity server host has an active DNS alias. |
|
Port: |
Port of the IdentityServer. |
|
LogPath: |
Contains the IdentityServer Logs (should be equal to the FireStartServer log path). |
|
DB-Path: |
IdentityServer stores user information in SQLite DB (default directory: <InstallPath>\FireStart Resources\Database). |
|
BaseURL: |
URL under which the External Search Provider is reachable. Attention: This host name has to be identical to the external Server name in the Basic Settings |
|
JWT Signing Certificate: |
The certificate used for signing the JWT token issued to the client. As recommendation, use the same certificate, as set in the basic settings. (If no value is provided, the default SSL Certificate is used, which is not recommended). |
|
Authentication Provider: |
The provider used for authentication. The following are supported: Windows (Default; Search Provider: Active Directory) Azure AD (Search Provider: Graph) SAML (SearchProvider: AD or External Search) |
| Active Directory Search | |
| Search user within OU: | Determines whether users in the FireStart people picker should be searched within own OU or in whole directory. |
| Domain1 | |
| Here, you define the domains, to which the FireStart server will have a relation. At least, one domain (Domain1) is required, additional ones (DomainN) can be added. | |
| Domain Name: | Name of the domain to be accessed. |
| FQDN (optional): | Full qualified domain name. (e.g. DC=prologics, DC=at to access the domain prologics.at) |
| Username (optional): | The user who can query this domain in the Active Directory. |
| Password (optional): | Password of the user who can query this domain in the Active Directory. |
| Use SSL (optional): | Select the “Use SSL” checkbox for the domain if you want to use LDAPS. |
Based on the selection of the Authentication/Search Provider, you may have additional settings:
For Azure AD (registering the application to Azure) and SAML (categorized under 'Relying Party Registration, External Search provider' and'ActiveDirectory'), other settings have to be defined as follows.
Azure AD (Register Application to Azure)

| Azure AD | |
|
Tenant ID: |
Either the ID of the Tenant or the name of the Azure instance. |
| Application ID: | From the Application Registration in Azure. |
| Application Secret: | From the Application Registration in Azure. |
|
Redirect URI: |
Redirect URI registered in Azure. Example: https://[server name].firestart.com/auth/sighin-oidc |
SAML (Relying Party Registration, External Search provider)

| SAML Authentication | |
|
Scheme: |
The schema name of the SAML profile |
| Partner IP Metadata Endpoint: | URL of the metadata endpoint of the SAML Authentication Provider. |
| Entity ID: | Registered Entity ID of the relying party. |
|
SAML Token Signing Certificate: |
The certificate used to sign the SAML tokens. |
| External Search Provider | |
| Base URL:
|
The URL of the external search provider |
SAML (ActiveDirectory)

| SAML Authentication | |
|
Scheme: |
The schema name of the SAML profile |
| Partner IP Metadata Endpoint: |
URL of the metadata endpoint of the SAML Authentication Provider., e.g. https://dc01.firestart-demo.com/federationmetadata/2007-06/FederationMetadata.xml |
| Entity ID: | Registered Entity ID of the relying party. |
|
SAML Token Signing Certificate: |
The certificate used to sign the SAML tokens. |
