If you want to use Azure AD authentication, you need to register an application for your FireStart Identity Server in the Azure portal.
Register the FireStart Azure Application
In the Azure portal go to Azure Active Directory > App Registration and click New Registration.

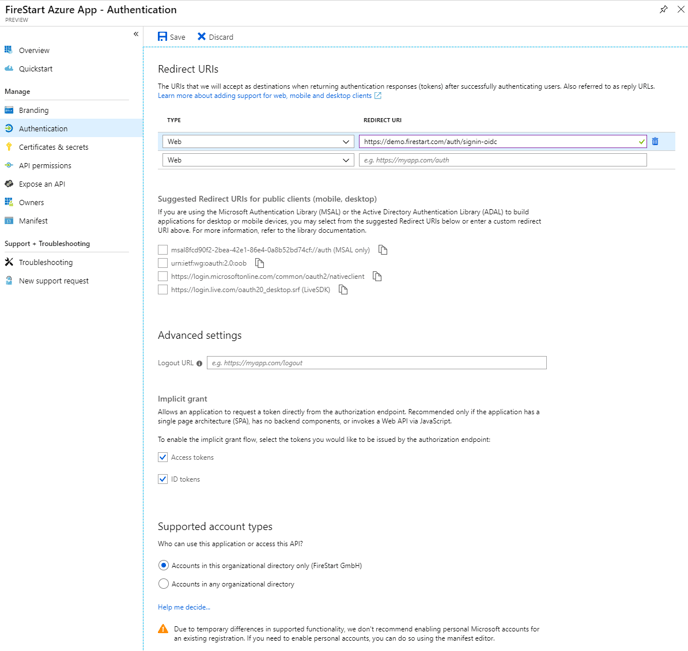
The redirect URI must not end with a subsequent slash.
Click on the newly registered app and you get to its Overview.

In the Manage category, click on Authentication. To enable the implicit grant flow, select Access tokens and the ID tokens.
Generate a new secret in Certificates & secrets

Do not forget to copy your secret before moving on.
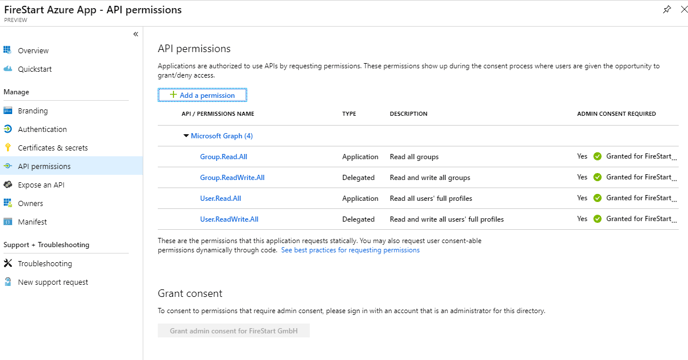
Next, go to the API permissions tab and add application permissions for User.Read.All and Group.Read.All and add delegated permissions for User.ReadWrite.All and Group.ReadWrite.All.
The last thing you have to do is to set the group membership claims in the manifest tab to All. The default value is null.
|
JSON
|
|
Now you have everything set up to configure the FireStart IdentityServer.
Configure the IdentityServer
To configure the IdentityServer, you need the Application (client) ID and the Directory (tenant) ID from the Overview tab. The Redirect URI from the Authentication tab and the secret you generated in the Certificates & secrets tab.
In the appsettings.json the Azure provider and the Graph search provider need to be enabled; all other (search) providers need to be disabled.
Provider Settings
- DisplayName: freely defined name for the provider.
- Scheme: an internal Identifier for the provider. Default set to "aad" for Azure Active Directory.
- TenantId: the name of the AzureInstance or the Azure TenantId.
- AppId: the Id of the app registration in Azure.
- AppSecret: the configured secret for the app registration.
Search Provider Settings
- DisplayName: freely defined name for the search provider.
- Scheme: same as in the provider settings.
- It is recommended to use the same configured application from the Azure portal for provider and search provider settings:
- TenantId: same as in the provider settings.
- AppId: same as in the provider settings.
- AppSecret: same as in the provider settings.
- RedirectUri: allowed redirect Uri for the app registered in Azure.
|
JSON
|
{
|
Do not forget to change the pesAdminGroup registry key to gDevelopment in order to start the FireStart server.
