If you want to use Windows authentication in FireStart, you need to ensure that Windows authentication is installed for IIS.

You can either install the feature via the Server Manager or you can use the configuration wizard.
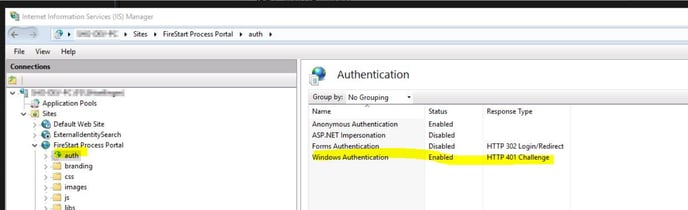
Also, be sure, Windows Authentication is enabled for HTTP 401 Challenge:
Configure the IdentityServer
The Windows provider and the Active Directory search provider need to be enabled in appsettings.json, and all other (search) providers need to be disabled.
Provider Settings
There are no additional settings for the Windows authentication provider.
Search Provider Settings
- Scheme has to be the same as in the provider settings. In this case, it has to be Windows
- SearchUsersWithinOU: if set to true, only admins search the complete directory, everyone else can only search for Users within their own organizational unit or sub-units
- Domains: a list of Domains in which to search, if no Domain is specified the Domain of the current server is used
- Domain: the domain name
- FQDN: optional
- Username: name of the user IS should use for active directory for search queries
- Password: encrypted password of the user with which IS searches for users
|
JSON
|
{
|
